On August 31, 2025, the Zscaler Data Breach was confirmed, exposing customer information after hackers compromised a Salesforce instance through Salesloft Drift OAuth tokens.
While Zscaler reassured customers that its security products and infrastructure were unaffected, the breach highlights a larger, recurring problem: the vulnerabilities created by SaaS-to-SaaS integrations.
- Hackers (UNC6395) used stolen OAuth tokens to bypass MFA and compromise Salesforce.
- Over 700 organizations were impacted, including Zscaler’s Salesforce environment.
- Exposed data: contact details + limited Salesforce case text (no passwords/financials).
- Breach may trigger GDPR/CCPA investigations and stricter SaaS security rules.
- Businesses must audit SaaS apps, enforce Zero Trust, and secure access (e.g., PureVPN WL).
For IT leaders, MSPs, and growing businesses, this breach serves as a warning that attackers don’t always need to break core security defenses. Instead, they exploit weaker, overlooked access points, like third-party integrations.
What Is Zscaler?
Zscaler is a leading cloud-native cybersecurity company best known for its Zero Trust Exchange platform. It provides secure access to applications, data, and services for enterprises worldwide, enabling safe hybrid and remote work environments.
Trusted by Fortune 500 companies and global enterprises, Zscaler is considered a backbone in the cybersecurity industry. That’s why the Zscaler Data Breach is particularly significant, if hackers compromised Salesforce at a company like Zscaler, every business using SaaS tools must reconsider how secure their integrations really are.
What Happened in the Zscaler Data Breach?
- Timeline: Between August 8–18, 2025, hackers compromised Salesforce OAuth tokens connected to Salesloft Drift.
- Threat Actor: Identified as UNC6395, a sophisticated group tracked by Google Threat Intelligence Group and Mandiant.
- Method: Using stolen OAuth tokens, attackers bypassed multi-factor authentication (MFA) entirely.
- Tools: Automated Python scripts were deployed to steal data from hundreds of organizations simultaneously.
Information Compromised
Zscaler confirmed that the breach exposed:
- Names, job titles, and business email addresses
- Phone numbers and regional details
- Salesforce-related licensing and commercial data
- Plain text from certain Salesforce support cases (excluding files or attachments)
While no passwords or sensitive financial records were stolen, the fact that hackers compromised Salesforce instance credentials is alarming.
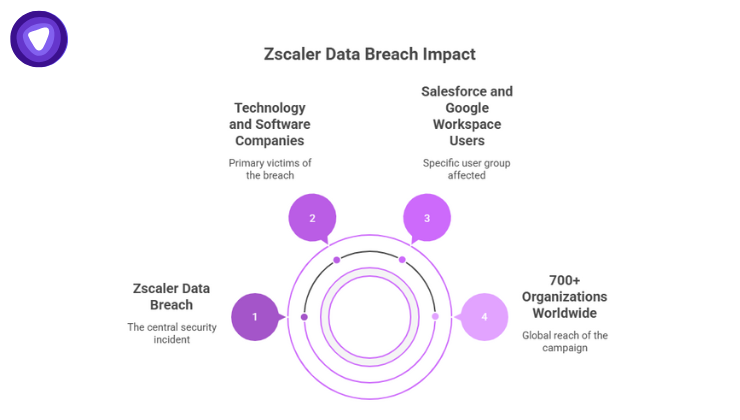
Who Was Impacted?
The Zscaler Data Breach was part of a much larger campaign that has already affected over 700 organizations worldwide. Most of the victims were technology and software companies deeply reliant on Salesforce and Google Workspace.
For Zscaler, only customer contact information and limited Salesforce case data were impacted. However, the breach underscores the cascading risk in SaaS ecosystems—where one weak link can potentially expose thousands of downstream businesses and clients.
Legal and Future Implications
The Zscaler Data Breach may also trigger legal and regulatory consequences for both Zscaler and Salesloft Drift. Under frameworks like the EU’s GDPR, the California Consumer Privacy Act (CCPA), and other global data protection laws, companies are required to disclose breaches promptly and can face hefty fines if negligence is proven. While Zscaler has stated the breach was limited to contact data, regulators may still investigate whether sufficient safeguards were in place for SaaS integrations.
Looking ahead, this case will likely influence future SaaS security standards. Expect tighter compliance requirements around OAuth token handling, third-party SaaS audits, and continuous monitoring of integrations. Vendors may also face increased customer scrutiny over how they secure interconnected services. For businesses, this incident sets a precedent: third-party SaaS risks will be treated as shared liability, meaning if hackers compromise Salesforce or other platforms through weak integrations, both the SaaS vendor and the customer could be held accountable.
Why This Matters
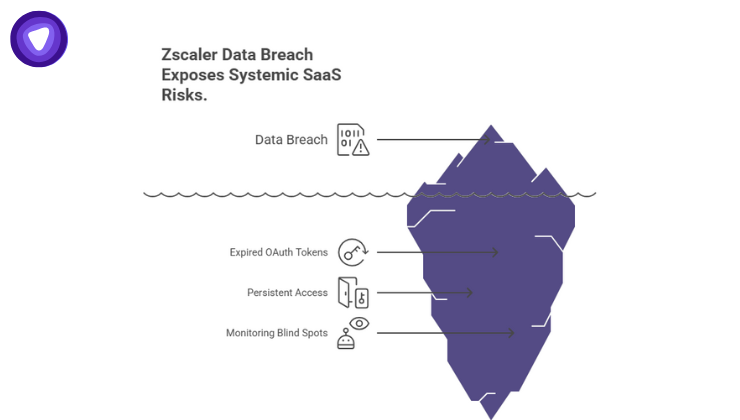
The Zscaler Data Breach highlights the systemic risk of modern SaaS environments:
- OAuth tokens rarely expire unless manually revoked.
- Once stolen, they allow persistent access without triggering MFA or password checks.
- Traditional monitoring tools often ignore token-based access.
This means attackers don’t need to breach hardened firewalls or servers, they just need to compromise a SaaS token.
Recent Similar SaaS Breaches
This isn’t the first time hackers have compromised Salesforce or other SaaS platforms. Over the past year, multiple breaches have highlighted the same weak point: third-party tokens and integrations.
| Company / Platform | Attack Vector | Impacted Data / Scope |
| Okta | Compromised customer support portal | HAR files with session tokens from ~134 customers |
| Cloudflare | Token reuse from Okta breach | Atlassian systems (Confluence, Jira, Bitbucket) |
| HubSpot | Unauthorized access to customer portals | Access to under 50 customer portals |
| Atlassian | Exploitation of software bug & credential leak | Personal data of ~13.2 million users |
| Slack | Stolen employee tokens used on GitHub | No customer data exposed; code repos accessed |
Pattern: Each case shows that once hackers compromise Salesforce instance tokens or SaaS integrations, attackers can bypass security controls silently.
How Businesses Can Prevent Similar Incidents
- Audit SaaS Connections: Regularly review integrations with Salesforce, Google Workspace, and other platforms. Revoke unused apps and apply least-privilege permissions.
- Monitor Abnormal Activity: Track large data exports or suspicious API queries.
- Enforce Secure Remote Access: Protect employees and clients with encrypted VPN tunnels.
- Educate Teams: Train staff to spot phishing campaigns that may follow breaches.
- Adopt Zero-Trust Networking: Continuously authenticate and verify every connection, internal or external.
Where PureVPN White Label Comes In
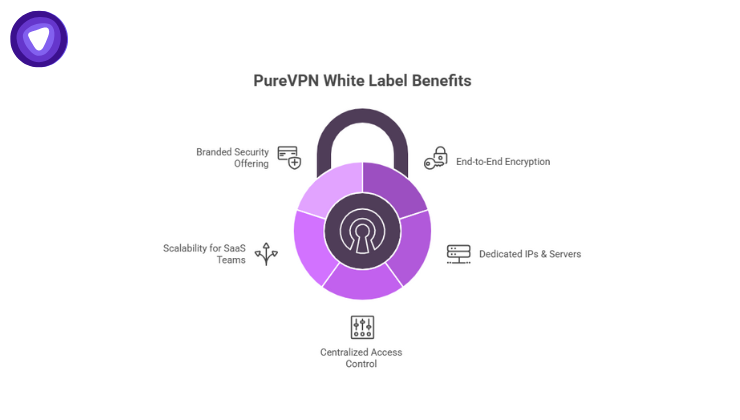
The Zscaler Data Breach makes one thing clear: businesses need stronger access security controls. With PureVPN White Label (WL), IT managers, MSPs, and service providers can launch their own branded VPN solution designed to mitigate risks like this.
Key features relevant to preventing incidents where hackers compromise Salesforce instances include:
- End-to-End Encryption: Every connection is encrypted, reducing the risk of token theft during data transfers.
- Dedicated IPs & Servers: Assign unique, controlled IPs for Salesforce or SaaS access, preventing unauthorized logins.
- Centralized Access Control: Monitor, manage, and restrict employee or contractor access to business-critical apps.
- Scalability for SaaS-Heavy Teams: Secure connectivity for 10 users or 10,000 without complexity.
- Branded Security Offering: Build customer trust by offering a VPN service under your own brand, backed by enterprise-grade infrastructure.
By routing Salesforce and SaaS connections through PureVPN WL, businesses can add a layer of control and visibility that token-based access alone cannot provide.
Final Thoughts
The Zscaler Data Breach reinforces an uncomfortable truth: cybersecurity is only as strong as the weakest integration. Even industry leaders with advanced defenses can fall when attackers exploit overlooked SaaS connections.
For businesses worldwide, this incident should be a call to action. Reviewing SaaS access, tightening integration security, and enforcing encrypted VPN usage are no longer optional, they’re essential.With PureVPN White Label, organizations can deliver branded, secure connectivity that protects their clients and teams from the next supply-chain attack. Don’t wait until hackers compromise Salesforce or another critical platform in your stack, secure your access today.


