In a move that’s drawn national attention and raised critical concerns about government overreach, DOGE Social Security Data access blocked by a federal court. While the headlines focus on the legal implications, the real story lies in what this moment means for businesses, platforms, and infrastructure providers.
This isn’t just a privacy story. It’s a warning about control, trust, and the systems we build around sensitive data. If you’re running any kind of digital business—especially one that handles user information—this affects you more than you think.
What Exactly Happened?

Let’s strip out the legal jargon.
DOGE, short for Department of Government Efficiency, was granted back-end integration with the Social Security Administration (SSA). The idea? Faster access to identity data to reduce paperwork. But what happened instead raised a red flag. DOGE started pulling unmasked Social Security records—with names, numbers, and other identifiers—without explicit individual consent.
Once exposed, the courts acted quickly. The result: DOGE’s access to Social Security data blocked, and all collected data was ordered deleted.
On the surface, it looks like the system worked. But underneath, this shows how quickly privacy can fall apart when safeguards are weak.
Why This Is a Red Flag for Private Sector Businesses?
You might think this is just a public sector issue. It’s not.
The real question is: how many integrations do you rely on that could silently expose your user data?
If DOGE can get backend access to millions of government records with little resistance, how hard do you think it is for vendors, APIs, plugins, and third-party tools to do the same in your system?
- What tools have persistent access to your customer PII?
- Are your authentication systems siloed or centralized?
- Do you log and monitor data access—internally and externally?
This isn’t theoretical. It’s operational.
What’s at Risk?
The average business doesn’t run national databases—but most collect enough user data to become targets:

- Names
- Contact info
- Behavioral data
- Payment details
- Internal credentials
If your systems don’t control who can access what, how it’s accessed, and when that access is triggered, you’re running on borrowed time.
DOGE didn’t need to “hack” anything. They were granted access under vague terms, without real-time alerts, without audit visibility, and without consent mechanisms.
That could happen to any unmonitored SaaS platform or database-driven service.
The Lesson? Centralization is the Problem
What DOGE Social Security Data Access Blocked revealed is a structural issue.
When you centralize access, permissions, and storage under one roof without separation or encryption, you create single points of failure.
This is true whether you’re a government agency or a 10-person startup.
The moment someone gets through—be it internal, external, or legal—you’ve lost visibility and control. The breach already happened.
Privacy-First Architecture Starts With Network Control
One of the simplest, most effective ways to prevent unauthorized access is to segregate your data access pathways. That starts with secure, encrypted networks, like VPNs.
A well-configured VPN infrastructure:
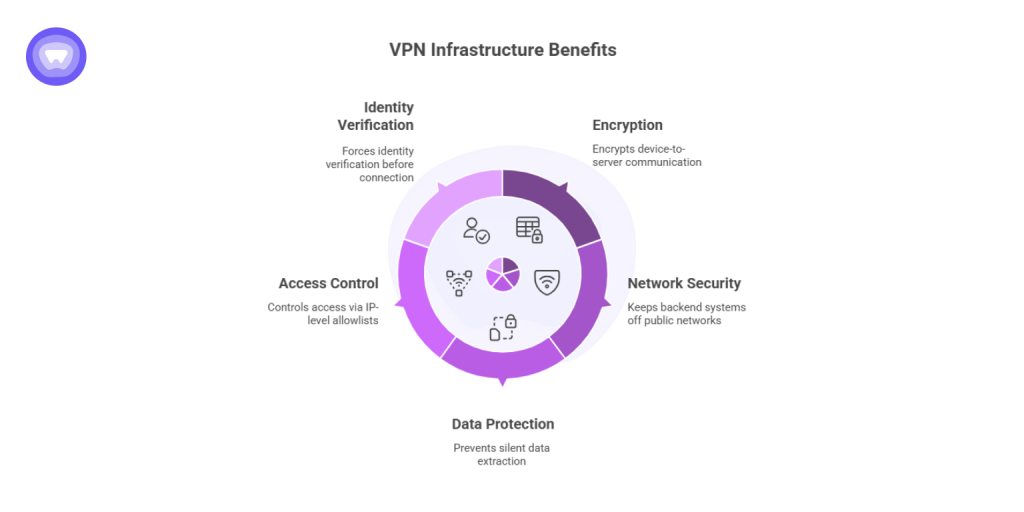
- Encrypts all device-to-server communication
- Keeps backend systems off public networks
- Prevents “silent” data extraction
- Controls access via IP-level allowlists
- Forces identity verification before connection
With white-label VPNs, your business doesn’t just use this protection—you provide it to your customers under your brand, with your policies, and your logs.
If DOGE Social Security Data Access Blocked didn’t get you thinking about secure access control, you’re missing the point.
Why White Label VPNs Make Business Sense Right Now?
Every business today is either collecting, processing, or hosting data.
With growing privacy laws and mounting customer expectations, security is no longer optional—it’s part of your product.
Getting a white labeled VPN solution means you can:

- Help your users secure remote access
- Create geo-restricted access policies
- Comply with privacy mandates (HIPAA, GDPR, etc.)
- Avoid exposing sessions to government surveillance or bad actors
- Improve your brand’s trust factor
All of this, without building your own infrastructure.
When you control the connection, you control the exposure.
The Oversight That Shouldn’t Have Happened
Let’s not gloss over the problem: DOGE got backend access to a federal data source without meaningful checks in place. That’s a failure of systems design.

- No API throttling
- No automated consent checks
- No encryption audit logs
- No alert escalation
When DOGE’s use of that access came to light, it had already happened. That’s the problem.
Now apply this to your business. If a team member, contractor, or vendor has “temporary” access to your customer records, who’s tracking it? Who’s auditing that activity in real time?
Too often, the answer is: no one.
What Should Businesses Do Now?
Here’s a checklist to future-proof your data strategy:

1. Audit Every Access Point
Map every system, API, and tool with access to your customer data. Who’s using it? What are the permissions? What gets logged?
2. Build a VPN Layer Into Your Internal Stack
All admin systems, backend tools, and customer dashboards should be behind VPN protection. You control traffic, location, and access.
3. Offer VPN to Your Customers
Don’t just protect your business. Help your users protect themselves. Especially if your product handles sensitive activities.
4. Control IPs and Endpoints
Set static IP rules for admin use. If someone’s working remotely, they should only connect through your branded VPN.
5. Use Monitoring and Anomaly Detection
If a tool, user, or department accesses more data than normal, your system should know—and flag it.
We Build the Network So You Can Control It
At PureWL, we help privacy-first businesses take ownership of their connection infrastructure. That means:
- Your brand
- Your encryption
- Your logs
- Your control
With a white-label VPN, you’re not relying on third-party services with murky data practices. You set the policy. You decide who connects, when, and from where.
Whether you serve clients in law, healthcare, consulting, education, or enterprise SaaS—you need to offer secure access that you own.
The world just saw what happens when access gets out of hand.
We make sure it doesn’t happen to you.
Final Takeaway
The headline “DOGE Social Security Data Access Blocked” is about more than overreach. It’s about how vulnerable even the most “secure” systems are when no one’s watching.
You don’t have to run a government agency to learn from this. You just need to take access seriously.
Control who sees what. Encrypt what matters. Make privacy part of your product, not just a line in your policy.
If you don’t own your infrastructure, someone else does.
And next time, that someone might not ask permission before using it.


