- ARP Mapping: ARP maps IP addresses to MAC addresses, enabling devices on a local network to communicate efficiently.
- ARP Tables: Devices use ARP tables to store IP-to-MAC mappings, reducing unnecessary broadcast traffic.
- ARP Variations: Variations like Proxy ARP, Gratuitous ARP, and RARP serve different roles in networking and legacy systems.
- ARP Spoofing: ARP is vulnerable to spoofing attacks, which can intercept traffic, hijack sessions, and steal credentials.
- VPN Security: Solutions like PureWL White Label VPN help secure networks by encrypting traffic and mitigating ARP-level attacks.
Modern networks depend on fast, precise communication between devices. Every message, every file transfer and every service call relies on one foundational step. A device must know exactly where to send the data. Before any connection is established on a local network, Address Resolution Protocol (ARP) performs the essential task of mapping an IP address to a physical MAC address.
This guide explains Address Resolution Protocol in a way beginners can understand while offering enough depth for technical readers. You will see how ARP works, why it matters, where it is used and how it introduces risks that organizations should not ignore.
Why Address Resolution Protocol Exists
On a local network, devices communicate using MAC addresses. Applications and services rely on IP addresses. These two addressing systems operate at different layers, so the network needs a translator.
Address Resolution Protocol fills that role. It connects an IP address with a MAC address to ensure packets reach the correct device. Industry research in 2024 showed that local network traffic still represents more than 65 percent of internal enterprise communication, which means ARP remains vital for daily operations.
Without Address Resolution Protocol, basic communication inside a LAN would fail. DNS resolutions, file transfers, remote sessions and even internet access would break because the final step in packet delivery would be incomplete.
Address Resolution Protocol Explained
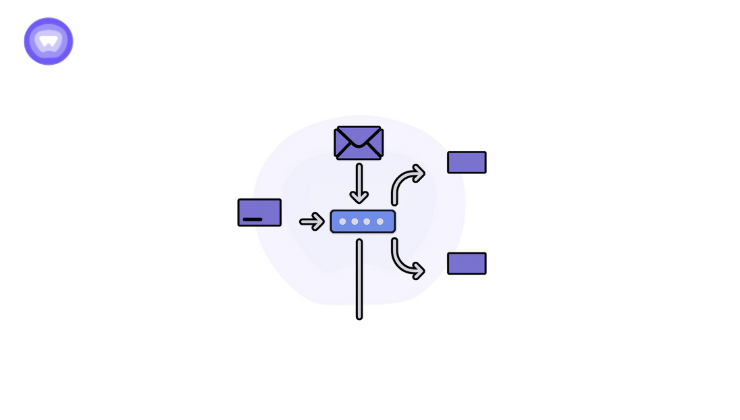
Address Resolution Protocol is a procedure used by devices inside a local network to identify the MAC address associated with a specific IP address. ARP operates within the data link layer and does not rely on TCP or UDP. This means it has no traditional port number.
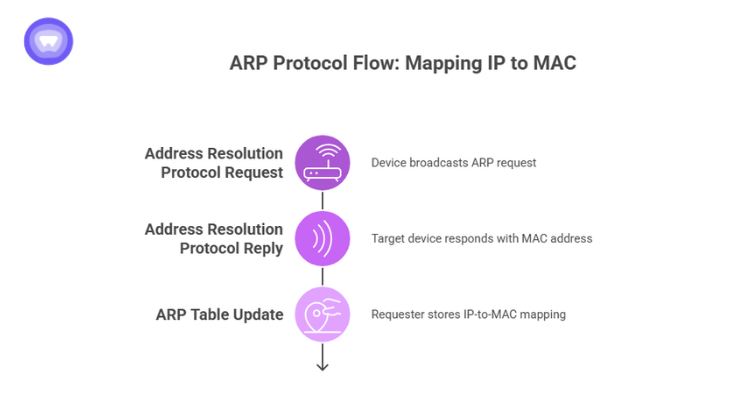
Here is the typical flow:
1. Address Resolution Protocol Request
When a device wants to send data and knows only the IP of the target, it broadcasts an ARP request. This request asks which device on the network owns that IP.
2. Address Resolution Protocol Reply
The correct device responds with its MAC address. The reply is unicast, sent directly to the requester.
3. ARP Table Update
The requester stores this IP-to-MAC mapping in its ARP table. This eliminates the need to broadcast again for the same device until the entry expires.
A network study found that ARP caching reduces broadcast noise by over 80 percent in busy office environments.
What Is an ARP Table and How Does It Work
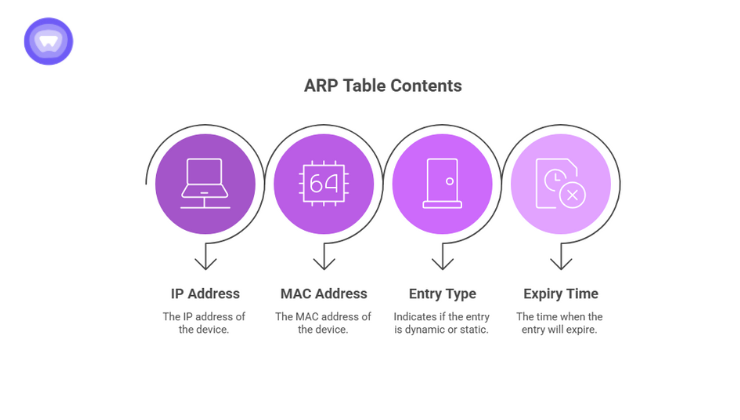
An ARP table (or ARP cache) stores known IP-to-MAC mappings. It usually contains:
- IP address
- MAC address
- Entry type (dynamic or static)
- Expiry time
Dynamic entries expire automatically after a short interval, commonly between 60 and 120 seconds, depending on the operating system. Static entries stay permanently until removed by an administrator.
Devices consult the ARP table before sending any request. This speeds up communication and reduces unnecessary broadcasts.
Types of Address Resolution Protocol (ARP)
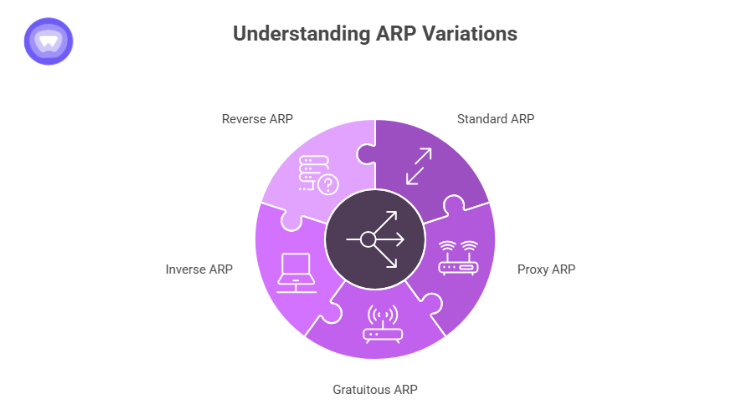
ARP has several variations that serve different roles in computer networks.
Standard ARP
Used for basic IP-to-MAC mapping inside any LAN.
Proxy ARP
A router responds to ARP requests on behalf of another network, allowing devices in separate subnets to communicate without knowing each other’s routes.
Gratuitous ARP
A device sends an unsolicited ARP reply to announce its presence or update other devices with its new MAC address. This helps prevent duplicate IP conflicts.
Inverse ARP (InARP)
Used mainly in Frame Relay and ATM environments. A device learns the IP address of another device from its known data link connection.
Reverse Address Resolution Protocol (RARP)
Reverse ARP allows a device that knows only its MAC address to request its IP address. RARP was used heavily by diskless workstations. It is now replaced by BOOTP and DHCP, which offer greater flexibility.
Reverse Address Resolution Protocol in Computer Networks
Reverse Address Resolution Protocol had one important job. It assigned an IP address to a device that lacked storage to save configuration data. RARP used a dedicated RARP server that responded to these requests.
Today, DHCP handles this role. However, Reverse Address Resolution Protocol remains part of networking history and influences modern bootstrap mechanisms.
Address Resolution Protocol Port Number
ARP is not tied to any port number because it does not use TCP or UDP. ARP functions inside Ethernet frames and communicates directly at the link layer. This is one reason ARP is efficient but also a reason it is targeted during internal attacks.
Address Resolution Protocol Spoofing
ARP has no authentication. Any device can respond to an ARP request, even if it does not own the IP address. This gap allows an attacker to send false ARP replies that poison ARP tables in the network.
Effects of ARP spoofing
- Traffic interception
- Session hijacking
- Credential theft
- Network disruption
- Man in the middle attacks
Security researchers reported in 2024 that ARP spoofing activity rose by 28 percent in co-working spaces and shared Wi-Fi networks. Attackers prefer ARP spoofing because it is quiet, fast and difficult to detect without monitoring tools.
Address Resolution Protocol in Computer Networks
ARP appears across every device that participates in LAN communication. It operates in:
- Office networks
- Data centers
- Public Wi-Fi networks
- Home network
- Virtualized environments
- Containers and overlay networks
Even cloud workloads use virtualized forms of Address Resolution Protocol to translate IP traffic between virtual network interfaces.
Address Resolution Protocol Example
A device with IP 192.168.1.10 wants to reach 192.168.1.25.
It checks its ARP table. If the MAC address is missing, it broadcasts an ARP request.
The device that owns 192.168.1.25 replies with its MAC address.
The requester stores the entry and sends the actual data.
This simple exchange happens constantly. A mid-sized network running 200 to 300 devices may generate thousands of ARP requests every hour.
Address Resolution Protocol Configuration
Administrators can manage ARP behavior to improve stability and security. Common tasks include:
- Adding static ARP entries for critical systems
- Changing ARP timeout values
- Clearing outdated ARP entries
- Using switch-level security such as Dynamic ARP Inspection
- Blocking unknown ARP replies
- Monitoring repeated ARP broadcasts
These adjustments help maintain predictable network behavior and reduce spoofing risks.
Key ARP Concepts Explained
Here are the key concepts of ARP and their functions, which help you understand how devices communicate on a local network.
| Concept | Description |
| Address Resolution Protocol | Maps IP address to MAC address inside a LAN |
| ARP Table | Stores IP-to-MAC mappings temporarily |
| ARP Request | Broadcast asking for the MAC of a specific IP |
| ARP Reply | Response containing the MAC address |
| ARP Spoofing | Attack that injects false IP-to-MAC entries |
| Reverse ARP | Finds IP address using a MAC address |
| Proxy ARP | Router answers ARP requests for remote networks |
| Gratuitous ARP | Unsolicited ARP message to announce or update address |
| ARP Port Number | Not applicable; ARP uses no TCP or UDP ports |
How ARP Requests and Replies Work
When a device wants to communicate on a local network, it first checks its ARP table to see if it already knows the MAC address associated with the target IP. If it does not, it sends out a broadcast ARP request to all devices on the network.
The device that owns the requested IP responds directly with its MAC address. Once this information is received, the requesting device updates its ARP table and can send data directly to the target device.
The sequence of these steps is often illustrated in an ARP diagram, which visually explains how ARP requests and replies flow between devices. This process happens automatically and continuously, ensuring that devices can communicate efficiently across the network without unnecessary broadcasts.
Where PureWL White Label VPN Fits Into ARP Security
ARP spoofing becomes a serious concern in shared networks, public Wi-Fi environments and untrusted LANs. PureWL White Label VPN helps reduce exposure by ensuring all traffic moves inside a secure, encrypted tunnel once the device connects to the VPN network. Even if an attacker attempts ARP-level manipulation, the intercepted packets remain unreadable.
PureWL White Label VPN also gives partners the ability to deliver a consistent, branded VPN experience to their clients. This includes controlled access, encrypted communication across teams and secure routing that prevents local attackers from inspecting or altering data.
Closing Thoughts
Address Resolution Protocol may seem simple, but it remains one of the most important processes inside computer networks. It handles every internal connection, populates the tables that keep communication efficient and helps devices identify each other with accuracy. Organizations that understand ARP gain better visibility into their own networks and can apply stronger security controls in areas where local attacks are most common.