- Over 60% of data breaches in 2025 involve stolen or misused credentials.
- Hackers use stolen logins to quietly access systems and steal data.
- Credential theft includes passwords, API keys, and access gained by individuals who tailgate.
- Breaches with stolen credentials cost 32% more and often cripple small businesses.
- PureWL White Label Password Manager helps prevent these attacks with encrypted storage, access control, and full brand ownership.
When hackers steal data, it rarely starts with a dramatic system shutdown or ransomware pop-up. Most breaches begin quietly with stolen credentials. A single compromised password can open the door to servers, client data, and internal tools without triggering alarms. For managed service providers (MSPs), SaaS companies, and small businesses, that one gap can cost millions in losses and reputation damage.
In 2025, over 60% of data breaches involve stolen or misused credentials, according to Verizon’s Data Breach Investigations Report. These breaches are often invisible, unfolding through small access points rather than direct hacks.
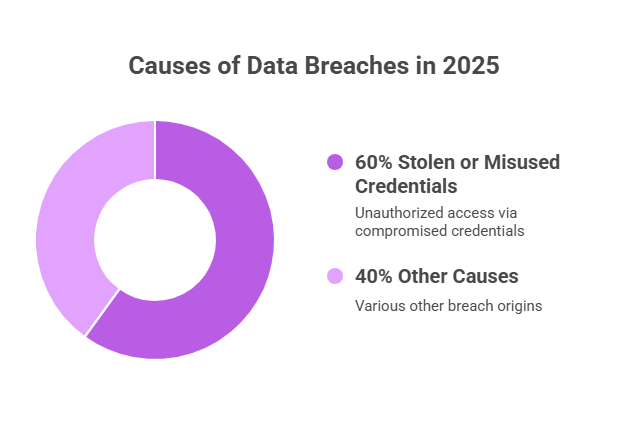
What Are Stolen Credentials?
Stolen credentials refer to any usernames, passwords, or authentication tokens that have been obtained illegally through phishing, malware, data breaches, or insider threats. Once compromised, these credentials allow attackers to impersonate legitimate users and access sensitive business systems, databases, or cloud services without detection.
They often appear in dark web marketplaces or private hacker networks, forming part of a global stolen credentials list traded among cybercriminals. For businesses, even a single leaked login can expose entire infrastructures, making credential theft prevention essential to maintaining operational and client security.
How Hackers Exploit Stolen Credentials?
Hackers use stolen credentials to move undetected through business systems. Once they gain access, they escalate privileges, install backdoors, or resell login data on dark web marketplaces.
Below are the most common tactics seen across industries.
| Attack Phase | Description | Example |
| Initial Access | Hackers use leaked passwords or phishing to log in like legitimate users. | Compromised employee email granting entry to internal dashboards. |
| Privilege Escalation | They use administrative credentials to widen control. | Gaining access to client billing systems or database servers. |
| Data Extraction | Sensitive data is downloaded or copied for later sale. | Exporting customer information from CRM platforms. |
| Persistence | Attackers create new hidden accounts or maintain API tokens. | Inserting new admin users into SaaS platforms. |
Each of these stages begins with something simple: credential theft.
Common Stolen Credentials Examples
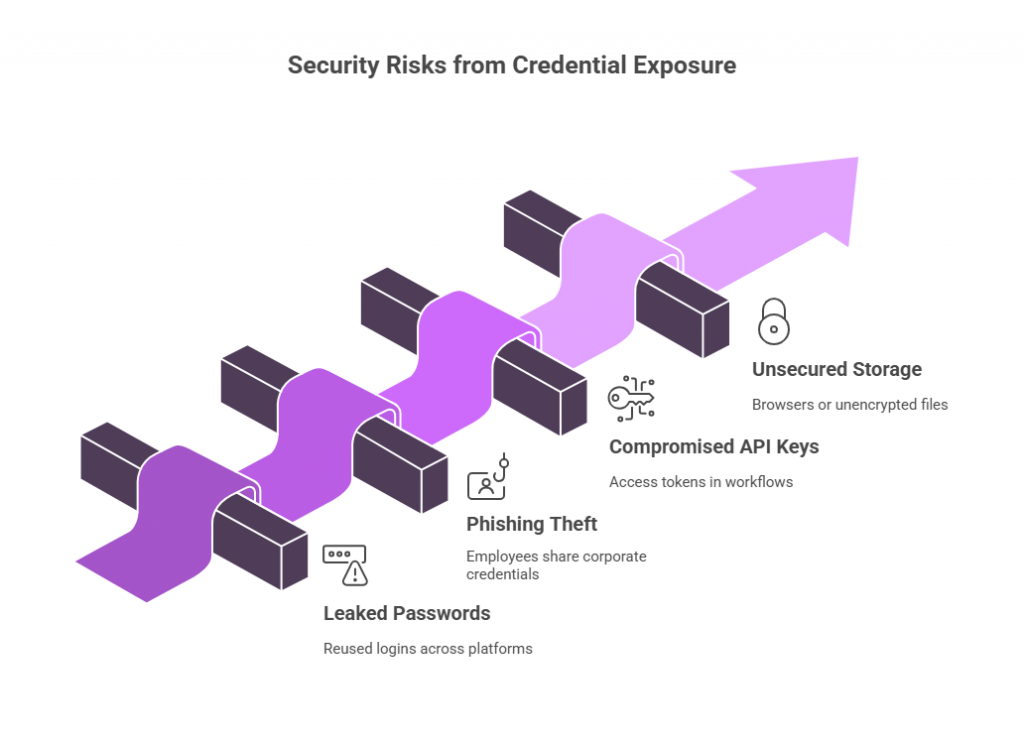
Understanding how credentials are stolen helps prevent future breaches. Some common stolen credentials examples include:
- Leaked passwords from reused logins across multiple platforms
- Phishing-based theft where employees unknowingly share corporate credentials
- Compromised API keys or access tokens used in automated workflows
- Unsecured password storage in browsers or unencrypted files
Even internal weaknesses, such as individuals who tailgate into secure office areas or shared terminals, can lead to physical compromise of accounts and hardware containing sensitive logins.
Why Credential Theft Is the Easiest Way In?
From a hacker’s perspective, credential theft is efficient, quiet, and profitable. They do not need to exploit zero-day vulnerabilities when they can simply log in with real usernames and passwords.
The MITRE ATT&CK framework lists multiple credential theft techniques under the “Credential Access” category, including brute force, credential dumping, and replay attacks. These tactics are widely used because they leave minimal forensic evidence, making stolen credential cybersecurity a critical defense layer for businesses of every size.
The Cost of Ignoring Credential Security
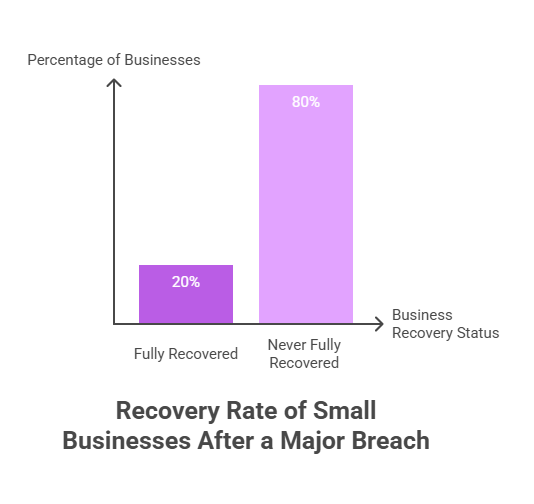
Credential breaches do not only affect large enterprises. SMBs and service providers face growing risk because they manage multiple client systems. According to IBM’s 2024 Cost of a Data Breach Report:
- The average breach costs $4.88 million, but when credentials are involved, costs rise by 32%
- 71% of businesses report credential-related phishing attempts every quarter
- Over 80% of small businesses that experience a major breach never fully recover operationally
This shows why credential theft prevention must go beyond employee training. It requires secure management systems, encrypted storage, and access control.
The Human Element In Stolen Credentials – Individuals Who Tailgate
While technical defenses are vital, individuals who tailgate into secure areas represent a physical threat vector. Tailgating, when someone follows an authorized person into a restricted zone, can allow threat actors to steal devices, capture credentials, or install malware directly.
This form of individuals who tailgate cyber security risk is often overlooked, yet it is part of the same credential theft chain. Once a system or device is accessed physically, attackers can extract stored passwords, session tokens, or authentication cookies.
Individuals who tailgate threat actor behavior aligns with broader insider or social engineering tactics. Businesses that rely on shared workspaces, remote teams, or flexible access models are particularly vulnerable.
The Expanding Stolen Credentials List
Today’s stolen credentials list extends far beyond basic usernames and passwords. Hackers target:
- Cloud service accounts (AWS, Azure, Google Workspace)
- VPN and remote access logins
- SaaS platform credentials for CRM, billing, or analytics
- Browser-saved passwords and autofill data
- API and developer tokens
This means credential protection is not only an IT responsibility. It is a business survival strategy.
What Actually Works For Credential Theft Protection?
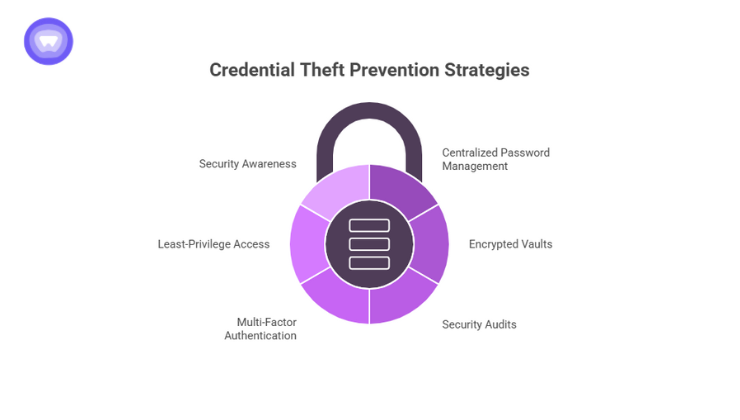
Effective credential theft prevention involves securing both the people and the processes that handle passwords. The best defenses include:
- Centralized Password Management
Store, manage, and share credentials securely across teams without revealing plain-text passwords.
- Encrypted Vaults and Zero-Knowledge Architecture
Ensure even the provider cannot access user data.
- Regular Security Audits and Access Reviews
Detect weak or reused credentials before they are exploited.
- Multi-Factor Authentication (MFA)
Add a layer of verification beyond passwords.
- Least-Privilege Access Policies
Limit system access only to what each user needs.
- Security Awareness and Tailgating Prevention
Train employees to spot suspicious behavior and control physical access points.
These steps collectively reduce the likelihood of breaches caused by stolen or mismanaged credentials.
How Businesses Can Build Stronger Password Infrastructure?
For MSPs and SaaS platforms that handle client data, deploying a branded password management solution offers long-term protection and control. Rather than relying on consumer-grade tools, a white-label model gives businesses ownership of both data and experience.
That is where the PureWL White Label Password Manager comes in.
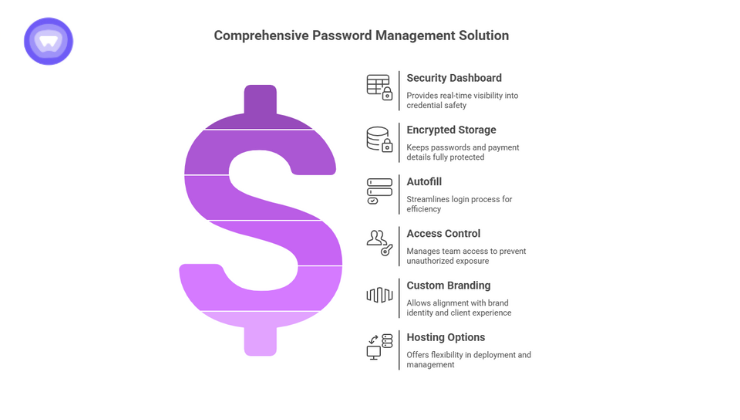
The PureWL White Label Password Manager enables businesses, MSPs, and SaaS providers to deliver a secure, branded password management service with full control over data and deployment. Its security dashboard provides real-time visibility into the safety of stored credentials, while encrypted storage keeps passwords and payment details fully protected.
With autofill and access control, teams can manage logins efficiently without risking unauthorized exposure. Custom branding and hosting allow providers to align the platform with their own brand identity and client experience. By adopting PureWL’s solution, businesses can strengthen protection and reduce stolen credential cybersecurity risks.
Take Control of Your Password Security
Using strong, unique passwords for every account is essential. A password manager makes it effortless to generate, store, and autofill complex passwords—keeping you safe from breaches.
Final Takeaway
Credential theft is not a futuristic threat. It is a daily, silent risk that grows with every reused password and unsecured login. From individuals who tailgate to phishing schemes and dark web trading, stolen credentials remain the foundation of most modern cyberattacks.
By adopting centralized, encrypted, and brand-owned password management through PureWL White Label Password Manager, businesses can secure their infrastructure, protect client data, and strengthen their position as trusted digital providers.


