- The Martinelli scam is a recurring WhatsApp hoax that spreads fake warnings and malicious links disguised as app updates like “WhatsApp Gold.”
- Although the video “Martinelli” doesn’t exist, clicking the link can lead to malware infections, credential theft, and device compromise.
- The scam’s success relies on fear, urgency, and social sharing, making it easy to resurface even years later.
- IT managers must strengthen device hygiene, access control, user awareness, and monitoring to prevent such threats.
- PureWL White Label VPN Solution helps secure remote teams by encrypting connections, protecting data, and ensuring safe communication across all devices.
The Martinelli scam has resurfaced in 2025, spreading rapidly across WhatsApp and other messaging platforms. These messages claim that a video named Martinelli can compromise devices, often coupled with a link to a fake app update.
While the threat appears straightforward, it poses significant risk to organizations, particularly those with remote or hybrid teams. Understanding how this scam operates and implementing strong credential and device management practices is critical for maintaining security and protecting sensitive data.
What is the Martinelli Scam?
The Martinelli scam refers to a chain message or post that circulates via WhatsApp (and other chat apps) claiming there is a “video” called Martinelli that, if opened, will hack your phone or compromise your data.
The message often couples this with an invitation to download a so‑called premium version of WhatsApp called WhatsApp Gold (or WhatsApp Plus) via a link. In reality:
- The video “Martinelli” does not exist.
- WhatsApp Gold is malware disguised as a legit app.
- The chain message uses fear (“nothing will fix it”) and urgency (“share with all contacts”) to amplify.
In other words: the Martinelli scam is a fear‑based hoax designed to get users to click unsafe links or download malicious apps.
Why is the Martinelli Scam Resurfacing in 2025?
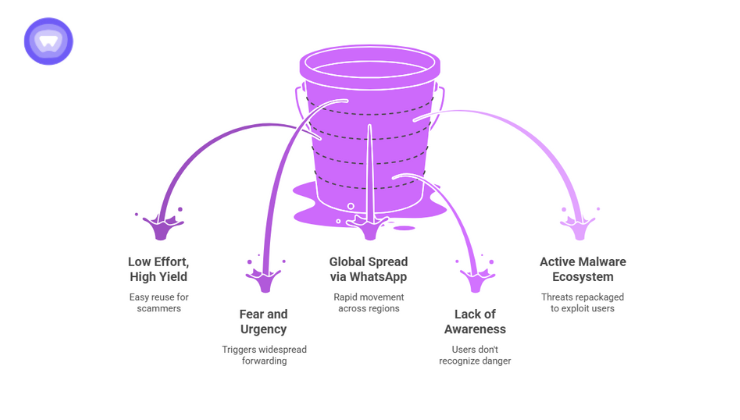
Although the Martinelli scam first appeared around 2016–2017, security researchers confirmed it resurfaced multiple times, reprising old messages with new twists.
Here’s why it keeps re‑emerging:
- Low effort, high yield: Once the template exists, it’s easy for scammers to reuse with minimal changes, gaining fresh victims.
- Fear + urgency work: The message triggers “share with everyone” behaviour, expanding its reach via organic forwarding.
- Global spread via WhatsApp: The platform’s group and forwarding mechanics help it move across regions quickly, even in 2025.
- Lack of awareness: Many users still don’t recognise that “update links” outside official stores are dangerous, so the familiar hoax still works.
- Malware ecosystem stays active: While the original “WhatsApp Gold” may be old, malware authors continue repackaging threats to exploit unsuspecting users.
How the Martinelli Sam Works: Step by Step
Here’s a breakdown of the usual sequence used by this scam:
| Step | What happens | Risk to user |
| 1 | You receive a forwarded message (text + maybe a fake screenshot) saying a video called Martinelli will be released tomorrow, don’t open it. | You become curious and concerned. |
| 2 | The message adds: “If you get a link to download WhatsApp Gold / WhatsApp Plus, do not click it.” | Suggests legitimacy (“see, they warn you”). |
| 3 | Somewhere in the thread is a link (often disguised) to download a “premium version” or “update”. | If clicked/downloaded: malware, data harvesting. |
| 4 | If you open the link, you might be asked for permissions, install an app, grant access etc. | Malware can steal contacts, media, credentials, or install further payload. |
| 5 | The message urges forwarding to all contacts “to warn them”. | Spreads the hoax rapidly. |
Security firm Sophos detailed a variant claiming the video was “Dance of the Pope” but using exactly the same template.
Why the “Video Hack” Angle Sticks
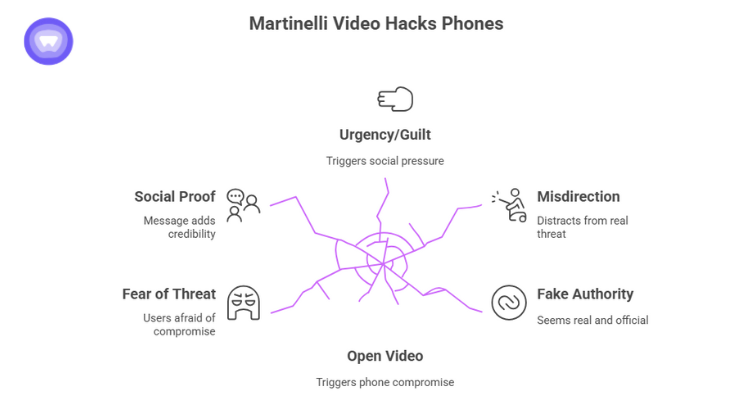
At first glance the claim “open video Martinelli = phone hacked, nothing will fix it” sounds dramatic, but several psychological triggers make it effective:
- Fear of unknown threat: Users are afraid their phone could be suddenly compromised.
- Social proof/faux legitimacy: The message often says “BBC radio announced it” or “IT colleague warned me” to add credibility.
- Urgency and guilt: “Forward to all your contacts so they don’t get hit” triggers social pressure.
- Misdirection: The video claim distracts from the real threat, the download link/malware.
- Fake authority: Using platform names (WhatsApp Gold) or official‑sounding references makes it seem real.
Understanding this psychology helps in crafting prevention, which is critical for IT managers responsible for distributed teams.
Impact of the Martinelli Scam on Devices and Organisations
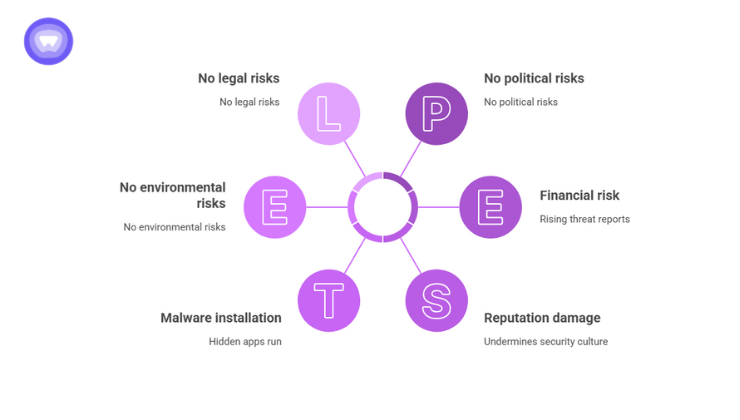
Though the video itself doesn’t exist, the risks posed by the associated malicious link or fake update are tangible. Some of the threats:
- Malware installation: Hidden apps can run in background, steal credentials, or join botnets.
- Credential harvesting: Contact lists, stored chat backups, local files may be exfiltrated.
- Lateral spread: On corporate‑owned devices or devices used for remote access, malware can enable broader compromise.
- Reputation & trust damage: If employees share hoaxes or malware in corporate chats, it undermines culture of security.
- Financial risk: According to Action Fraud data, threats via WhatsApp and social channels are on the rise, “more than 35,000 reports” in one year of social media/email account hacking.
For IT managers, especially in development or remote teams, the Martinelli scam highlights how even simple chain messages can cascade into real operational and security risk.
What IT Managers Must Do: Control and Defend

Here are actionable steps you can implement to defend against the Martinelli scam and similar threats:
1. Device and app hygiene
- Ensure mobile devices are running the latest OS versions.
- Block installations from unknown sources (for Android).
- Only allow apps from official stores.
- Use endpoint/mobile‑device management (MDM) tools to enforce policies.
2. Credential security and access control
- Enforce strong unique passwords for each service (no reuse).
- Enable multi‑factor authentication (MFA) across accounts.
- Use a dedicated password manager across team.
3. Awareness training for users
- Educate users that any message urging “forward to all” + “download link” = high risk.
- Emphasise that official app updates happen via app stores, not via chain links.
- Encourage reporting rather than forwarding messages to reduce spread.
4. Monitoring and detection
- Monitor unusual app downloads or network traffic from mobile devices.
- Deploy mobile threat defense solutions for scanning unknown or risky apps.
- Maintain inventory of devices and installed apps within your environment.
5. Incident response readiness
- Have a procedure if a device is suspected of compromise (isolate, wipe, restore).
- Ensure backups are available for critical mobile data.
- Communicate clear policy about personal devices accessing corporate resources.
How This Links to Password Risk and Remote Access
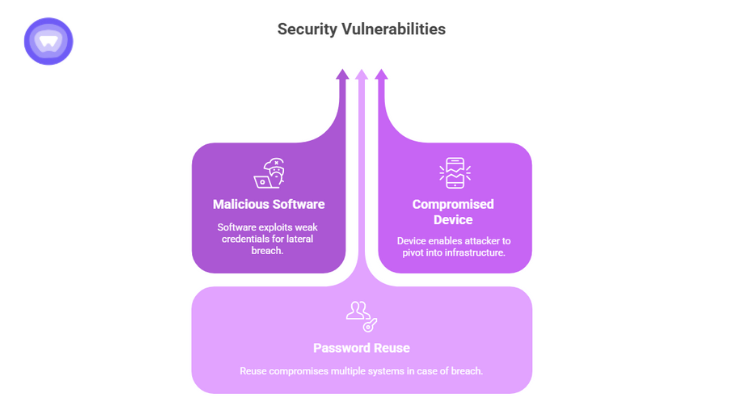
Mobile devices are often portals to sensitive resources, chat with clients, access code repositories, remote desktops. A user who falls prey to a message like the Martinelli scam may inadvertently expose credentials or tokens. Protecting the password layer is critical.
For instance:
- If malicious software gains access to your device, weak or reused credentials can allow lateral breach.
- A compromised device used for remote server access could enable the attacker to pivot into your infrastructure.
- Password reuse across team tools means a breach on one device can compromise multiple systems.
Therefore, as an IT manager you must consider the password‑management strategy as part of your overall security posture, especially in an era where even innocuous‑seeming messages can trigger device compromise.
Martinelli Scam at a Glance
These are the key aspects of the scam:
| Aspect | Key takeaway |
| Threat vector | Chain message claiming “video Martinelli” + link |
| Core lure | “Do not open video / download update” |
| Real risk | Malware disguised as “WhatsApp Gold” |
| Impact on organisation | Device compromise, credential theft, lateral spread |
| Key defense areas | Mobile hygiene, user awareness, password controls |
| Role of IT manager re password | Use strong unique passwords, enforce MFA, use dedicated manager |
Why the Martinelli Scam Remains Relevant for Remote Teams
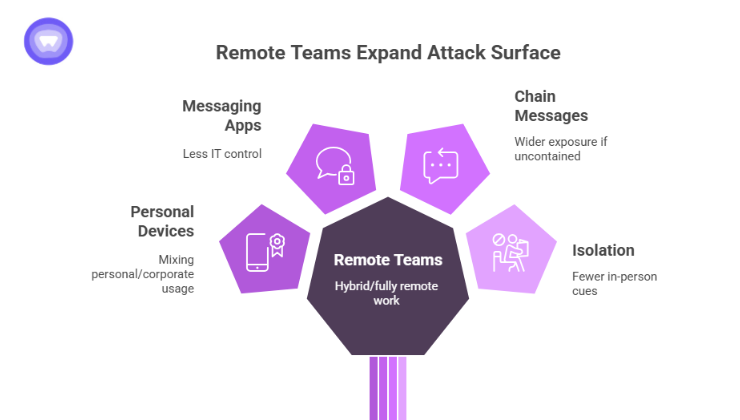
In 2025 many organisations still endorse hybrid or fully remote teams. This creates expanded attack surfaces:
- Team members may use personal devices or mix personal/corporate usage.
- Messaging apps like WhatsApp are integral to remote team communication and may be less controlled by IT than enterprise apps.
- A chain message may propagate in a team chat and cause wider exposure if not contained.
- Remote workers may be isolated, fewer in‑person cues to recognise hoaxes.
The Martinelli scam underscores the importance of integrating device/credential hygiene into your remote‑access strategy.
Securing Remote Teams with PureWL White Label VPN Solution
For organizations with remote or hybrid teams, safeguarding connections and sensitive data is crucial. PureWL White Label VPN Solution ensures secure, encrypted connections for all devices, protecting communications from threats like the Martinelli scam. By centralizing remote access security, it reduces the risk of malware spread or unauthorized access across the organization.
The solution is designed for teams of any size, providing consistent security policies without adding operational complexity. With PureWL White Label VPN Solution, IT managers can maintain control over network access while enabling seamless collaboration across locations.
Final Thoughts
Protecting organizational data and remote connections against scams like Martinelli requires robust, reliable tools. PureWL White Label VPN Solution delivers enterprise-ready security, encrypting traffic, securing devices, and giving IT teams confidence that sensitive communications remain safe, keeping distributed teams protected in a constantly evolving threat landscape.


