- F5 Breach Impact: Over 266,000 BIG-IP devices were exposed, affecting enterprises globally and critical infrastructures.
- Source Code Theft: Attackers accessed BIG-IP source code and internal documentation, enabling potential future exploits.
- Immediate Action Required: Organizations must patch systems, audit configurations, reset credentials, and harden access.
- Credential and Access Management: Centralized control over credentials and strict identity management are essential to limit risk.
- PureWL White Label VPN: Provides encrypted remote access, granular admin controls, and visibility to reduce exposure for F5-powered systems.
When network infrastructure fails, it doesn’t just expose data, it destabilizes entire business ecosystems. The F5 breach is a prime example. In late 2025, F5 Networks confirmed a major security incident that sent shockwaves through the enterprise community. The breach affected BIG-IP devices used globally across corporations, government networks, and financial systems.
This is not another routine vulnerability announcement. It’s a wake-up call about how dependent modern infrastructure has become on third-party network systems, and what happens when those systems are compromised.
What is F5 and Why the Breach Matters?
F5 is an American technology company best known for its BIG-IP platform, which handles network traffic management, application delivery, and security. BIG-IP devices sit at the core of data centers and cloud networks, ensuring uptime, scalability, and secure access for enterprise applications.
When a f5 security incident affects F5 itself, the implications ripple far beyond one company’s perimeter. These systems touch everything from financial APIs to government web portals. That is why the f5 breach today is being treated as one of the most significant infrastructure compromises of the decade.
How the F5 Breach Unfolded?
The f5 breach update reveals that attackers infiltrated F5’s internal development environment months before detection. They exfiltrated proprietary BIG-IP source code, internal documentation, and potentially undisclosed vulnerability details.
Security researchers later identified hundreds of thousands of BIG-IP devices accessible online, many still unpatched, making them potential targets for follow-up exploitation.
The Timeline of Key Events
The following table provides a concise breakdown of how the f5 breach evolved and the major milestones that shaped the response.
| Date | Event | Significance |
| August 9, 2025 | F5 detected a network intrusion within its development environment. | Indicates prolonged undetected access. |
| October 15, 2025 | F5 publicly disclosed the incident. | Triggered global alerts and scrutiny. |
| October 16, 2025 | CISA issued Emergency Directive 26-01 mandating immediate patching. | Signaled the national-level severity of the breach. |
| October 20, 2025 | Shadowserver found 266,978 exposed BIG-IP instances. | Confirmed the global attack surface. |
These events show how fast a contained incident turned into a worldwide infrastructure threat.
Scope of Exposure: The F5 Breach List
According to multiple security monitors, over 266,000 BIG-IP devices were exposed to remote attacks in the aftermath of the f5 breach list findings. Here’s what that means for enterprise security today:
- 142,000+ of these devices are located in the United States.
- 100,000+ are deployed across Europe and Asia.
- Many belong to public-sector, telecom, and financial institutions.
- Several are still running outdated firmware versions with known vulnerabilities.
This vast exposure explains why the CISA F5 breach alert demanded immediate action, F5 devices often sit at privileged network chokepoints, meaning a single compromise can cascade across systems.
Why This Breach Is Unprecedented?
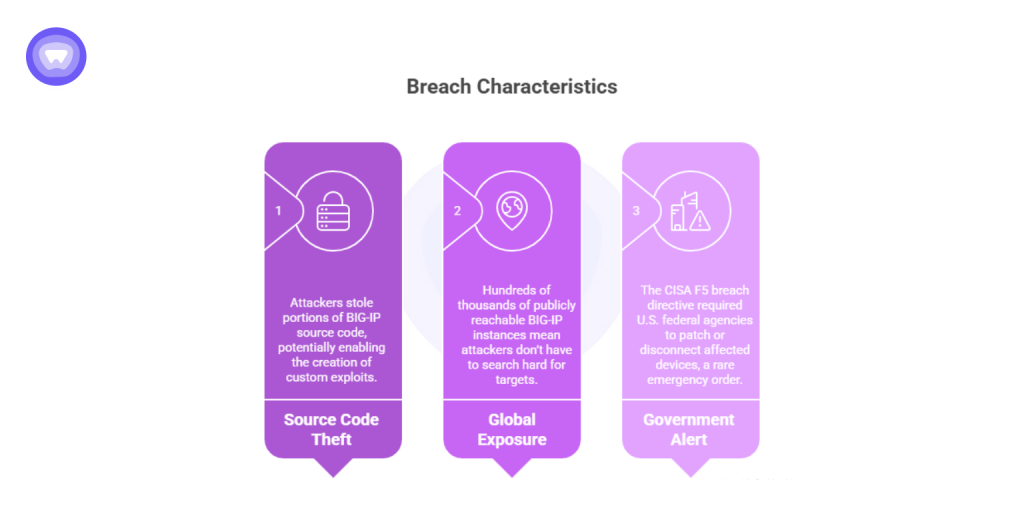
The f5 breach stands out because of the unique combination of scope, depth, and systemic impact:
- Source Code Theft: Attackers stole portions of BIG-IP source code, potentially enabling the creation of custom exploits.
- Global Exposure: Hundreds of thousands of publicly reachable BIG-IP instances mean attackers don’t have to search hard for targets.
- Government-Level Alert: The CISA F5 breach directive required U.S. federal agencies to patch or disconnect affected devices, a rare emergency order.
- Supply Chain Implications: Because BIG-IP integrates with countless vendors and networks, one vulnerability can propagate through entire ecosystems.
In essence, this isn’t just an F5 security incident, it is a supply-chain security crisis.
Immediate Actions to Take
Every organization using BIG-IP or related F5 technologies must treat this as a critical incident. Below are prioritized actions to protect your environment and limit exposure.
Step 1: Patch and Update Immediately
- Install all F5-issued patches for BIG-IP, BIG-IQ, and F5OS products.
- Decommission unsupported or end-of-life hardware.
- Verify that administrative interfaces are not publicly accessible.
Step 2: Audit Configurations and Access
- Inventory all F5 assets across data centers, cloud, and remote sites.
- Restrict access to management ports to trusted internal networks.
- Apply least-privilege controls for administrative users.
Step 3: Reset and Harden Credentials
- Rotate all credentials associated with F5 appliances and connected systems.
- Reissue API keys and enforce MFA for all privileged accounts.
- Validate that no unauthorized admin accounts exist.
Step 4: Enhance Monitoring and Response
- Enable detailed logging on all BIG-IP systems.
- Integrate logs with SIEM tools to detect configuration anomalies.
- Conduct targeted threat-hunting for lateral movement or persistence indicators.
These steps address the most immediate risks tied to the f5 breach today.
The Broader Security Impact
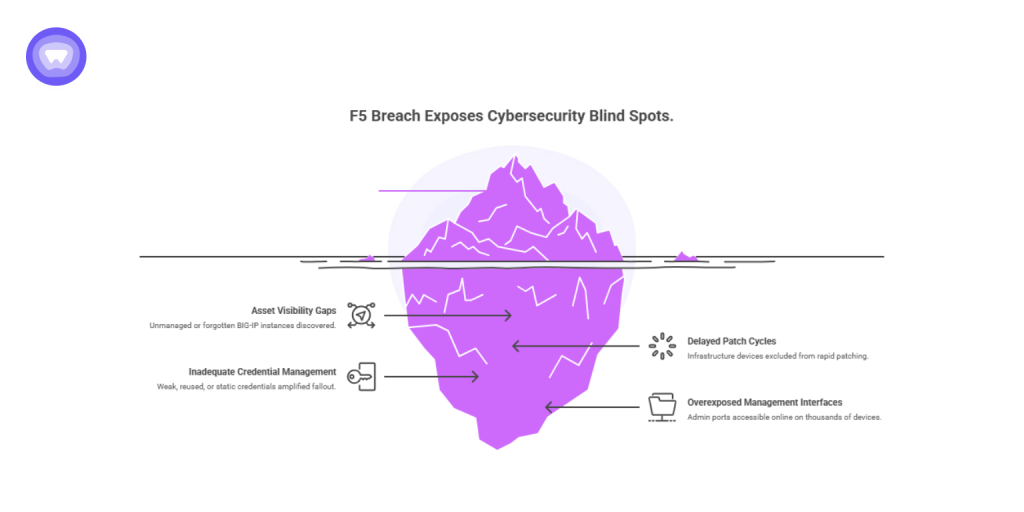
The f5 breach has exposed several blind spots across the cybersecurity landscape:
- Asset visibility gaps: Many enterprises discovered unmanaged or forgotten BIG-IP instances.
- Delayed patch cycles: Infrastructure devices are often excluded from rapid patching policies.
- Inadequate credential management: Weak, reused, or static credentials amplify the fallout.
- Overexposed management interfaces: Thousands of devices still have admin ports accessible online.
The breach highlights how critical it is to continuously review configurations, enforce strict access controls, and centralize credential management.
The Real Risk: Persistent Access
The danger doesn’t end once systems are patched. Because attackers obtained internal documentation and parts of BIG-IP source code, they could identify vulnerabilities not yet disclosed publicly.
This increases the likelihood of zero-day exploitation in the near future.
That is why monitoring for suspicious network behavior and enforcing strict identity management remain non-negotiable. Even a minor lapse in access hygiene can reopen the door.
Key Lessons for Security Teams
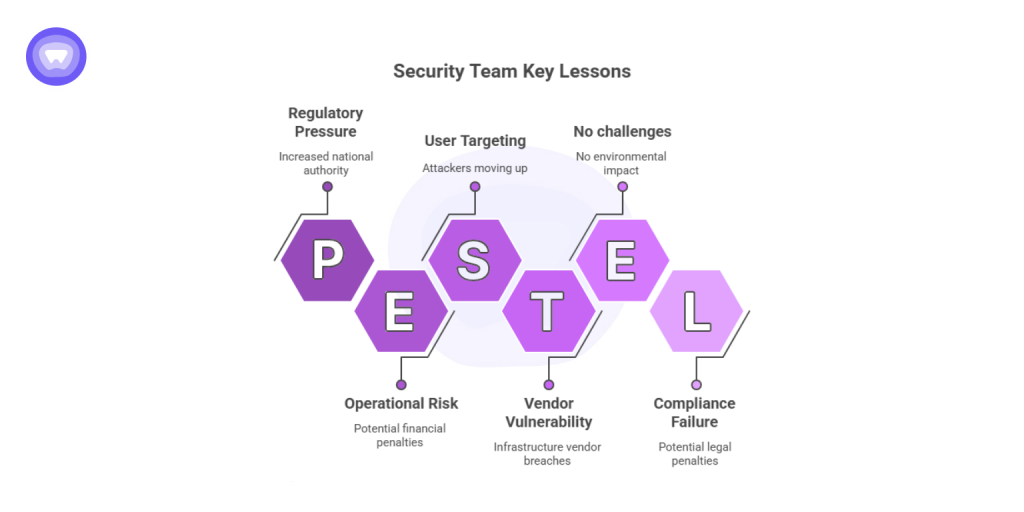
Organizations that fail to act will not only face operational risk but potential regulatory penalties as well.
- Vendor trust is not immunity. Even established infrastructure vendors are vulnerable.
- Attackers are moving up the stack. Instead of targeting users, they now exploit the technologies that secure them.
- Credentials remain a primary weakness. Many F5 breach Reddit discussions reveal unrotated keys and reused admin passwords still in use.
- Regulatory pressure is increasing. The CISA F5 breach directive shows how seriously national authorities now treat infrastructure vulnerabilities.
Security Checklist for Organizations
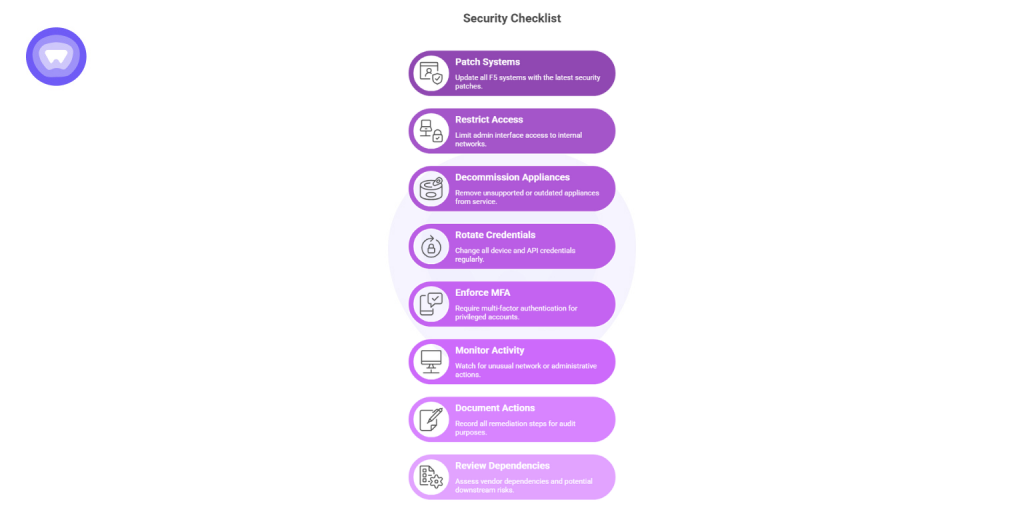
Use this practical list to evaluate your readiness in the wake of the f5 breach:
✅ Patch all BIG-IP and F5 systems with the latest security updates
✅ Restrict admin interface exposure to internal networks only
✅ Decommission unsupported or outdated appliances
✅ Rotate all device and API credentials
✅ Enforce MFA for all privileged accounts
✅ Monitor for unusual network or admin activity
✅ Document all remediation actions for audit trails
✅ Review vendor dependencies and downstream exposure
A disciplined, proactive approach is the only way to contain long-term impact.
Strengthening Access Security with PureWL White Label VPN Solution
The F5 breach highlights a critical need for centralized control over credentials and secure network access. PureWL White Label VPN solution enables businesses to protect their infrastructure through encrypted connections and by isolating sensitive management interfaces from public exposure.
With secure remote access, granular admin controls, and full visibility over credential usage, PureWL helps organizations using F5-powered systems minimize attack surfaces and prevent unauthorized access.
Moving Forward
The f5 breach is a defining moment for infrastructure security. Over 266,000 devices remain potentially exposed, and attackers now possess knowledge that could inform future, stealthier exploits.
Whether you operate in finance, cloud services, or IT management, your network’s integrity depends on how fast and effectively you act now. Patch systems, secure credentials, and harden access controls, because the next breach may not offer a second warning.


