- TruffleNet redefined cloud threats: It used stolen AWS credentials instead of malware to carry out large-scale fraud.
- Attackers exploited trust: Every action used legitimate AWS API keys, making detection extremely difficult.
- Key service abused: Amazon SES was weaponized for global phishing that passed all authentication checks.
- Lesson for IT leaders: Credential hygiene and access control are now central to cloud defense.
- PureWL’s role: Encrypted, authenticated VPN access ensures cloud credentials are only used securely.
In late 2025, researchers uncovered a cyber campaign that changed how experts view cloud security. Known as the TruffleNet attack, it did not depend on malware, zero-day exploits, or brute-force intrusions. Instead, it weaponized something far more ordinary, legitimate AWS credentials.
By gaining access to real Amazon Web Services (AWS) access keys, attackers turned trusted infrastructure into an engine for global fraud. What began as a few leaked credentials evolved into an industrial-scale operation that blurred the line between authorized activity and abuse.
This event signaled a new chapter in cyber warfare, one where logging in has replaced breaking in, and identity is now the true perimeter.
The New Face of Cloud Exploitation
Most cloud incidents stem from code vulnerabilities or misconfigured servers. TruffleNet took a different path, exploiting trust itself. Every action in this campaign was carried out using valid, authorized AWS API keys.
Once inside, the attackers used AWS’s own services, particularly Simple Email Service (SES), to distribute thousands of fraudulent messages. Because SES is inherently trusted by most spam filters, these emails, complete with verified SPF, DKIM, and domain headers, appeared authentic to victims.
This strategy allowed TruffleNet to bypass traditional defenses and demonstrate how attackers can weaponize legitimate cloud ecosystems.
How the TruffleNet Operation Worked
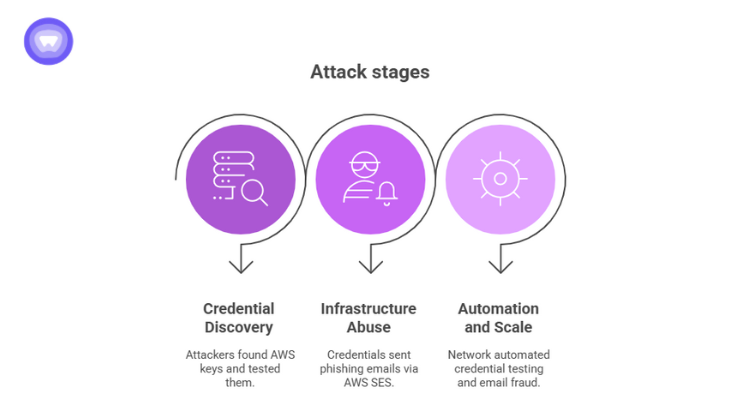
Unlike opportunistic phishing attacks, TruffleNet followed a structured, multi-phase playbook designed for scale and resilience.
1. Credential Discovery
Attackers collected AWS keys from publicly exposed repositories, outdated configuration files, and compromised developer environments. These keys weren’t privileged admin logins, just overlooked, valid tokens with enough permissions to get started.
Using automated tools, they performed reconnaissance by making safe, low-profile API calls. One common pattern was checking the SES send quota to determine whether a key had active permissions.
Within weeks, researchers observed over 800 servers across 57 networks involved in testing, verifying, and exploiting these credentials.
2. Infrastructure Abuse
Once they confirmed which accounts had usable permissions, attackers weaponized them. They configured new sender identities, enabled DKIM authentication, and began distributing invoice and payment scams that closely resembled legitimate business correspondence.
Each email passed authentication checks and came from verified domains, making it nearly indistinguishable from genuine communication.
3. Automation and Scale
TruffleNet wasn’t a small-scale fraud ring, it functioned like a production pipeline.
- Recon nodes validated credentials and tested API limits.
- Abuse servers sent large email volumes through AWS SES.
- Management nodes coordinated domains, quotas, and timing.
This degree of automation allowed the campaign to operate continuously, harvesting and exploiting new credentials almost in real time.
What Made TruffleNet Different
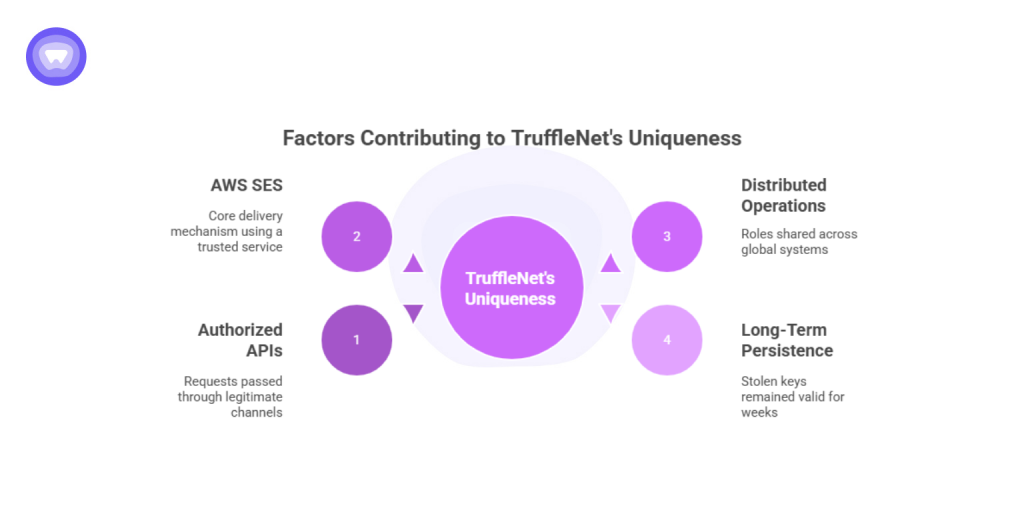
The TruffleNet attack stood apart from typical breaches for several reasons:
- No malware or exploits: Every request came through authorized APIs.
- Legitimate infrastructure: AWS SES was used as the core delivery mechanism.
- Distributed operations: Hundreds of global systems shared roles, making detection difficult.
- Long-term persistence: Stolen keys often remained valid for weeks, allowing repeated abuse.
In essence, the attackers didn’t break into AWS, they simply borrowed its keys.
Why AWS Credentials Became the Perfect Weapon?
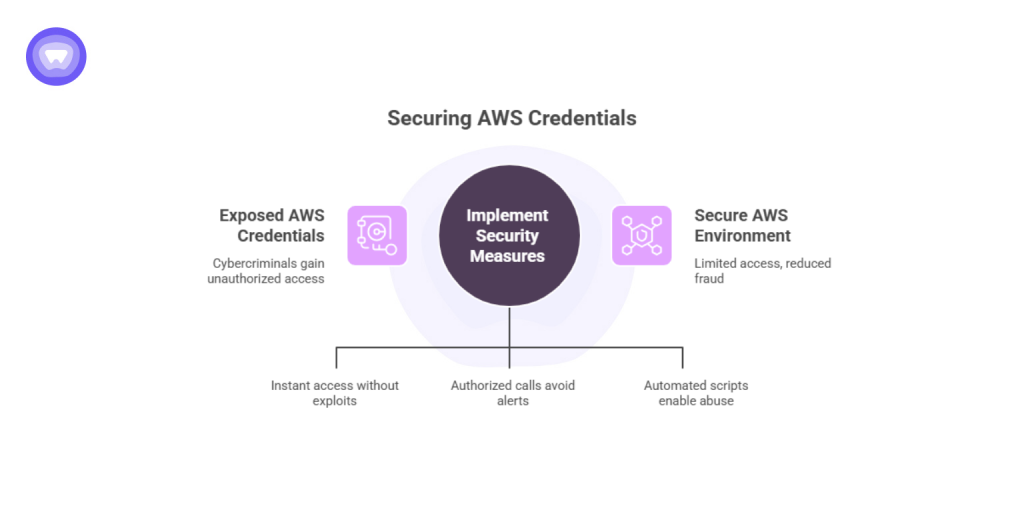
For cybercriminals, exposed AWS credentials are gold. One leaked key can unlock access to storage, computing, or messaging services, creating endless opportunities for fraud.
Over 80% of cyberattacks now leverage stolen or compromised credentials.
The TruffleNet group capitalized on this by focusing on:
- Speed: Valid credentials gave instant access without needing exploits.
- Stealth: Authorized calls rarely trigger intrusion alerts.
- Scalability: Automated scripts enabled 24/7 credential testing and abuse.
Their success highlighted that efficiency, not sophistication, is now the hallmark of modern cybercrime.
The Global Fallout
TruffleNet’s reach was global, with fraudulent emails targeting multiple industries and continents. Many victims received fake invoices or tax updates that appeared to come from verified supplier domains.
In one verified incident, attackers spoofed a vendor’s domain by replacing the reply-to address with a typosquatted variant ending in “-impactaction.com.” The deception was subtle enough to fool accounting teams into transferring funds to attacker-controlled accounts.
The campaign effectively merged Business Email Compromise (BEC) tactics with cloud credential abuse, creating a hybrid threat that blended legitimacy with deception.
Key Findings from the TruffleNet Investigation
These are the main highlights from the attack:
| Threat Element | Observed Behavior | Security Implication |
| Credential Source | Leaked AWS keys from GitHub, code archives, and developer systems | Inadequate secret management remains a major attack vector |
| Reconnaissance Activity | 800+ hosts validating credentials via AWS APIs | Highly distributed infrastructure complicates detection |
| Abused Service | Amazon Simple Email Service (SES) | Trusted infrastructure used for global-scale phishing |
| Attack Outcome | Business Email Compromise (BEC) and vendor payment fraud | Direct financial and reputational damage |
| Detection Challenge | API requests appeared legitimate | Signature-based systems often failed to trigger alerts |
Lessons for Cloud and Security Leaders
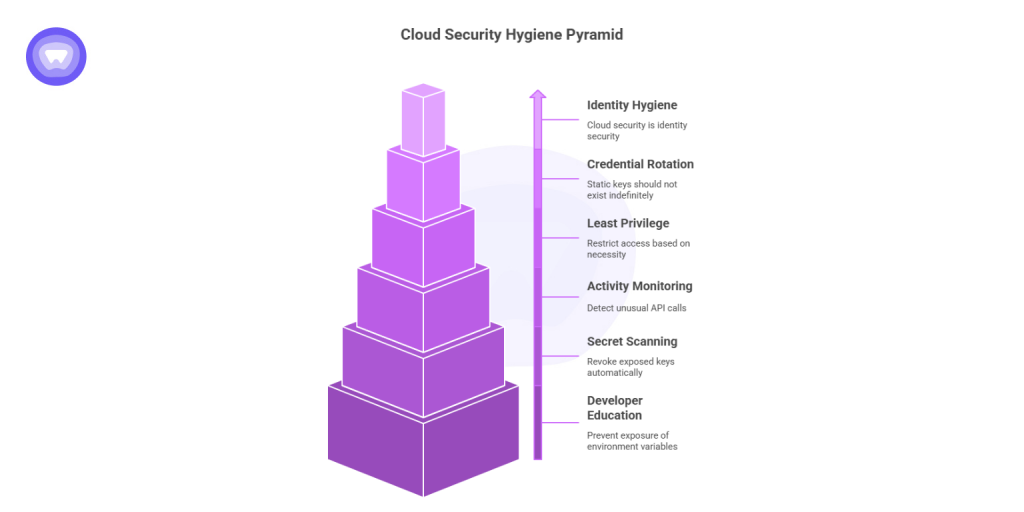
TruffleNet proved that cloud security hygiene is identity hygiene. For organizations that rely on AWS or similar platforms, protecting access keys must become a top operational priority.
- Rotate credentials frequently: Static access keys should never exist indefinitely.
- Enforce least privilege: Restrict what each credential can do.
- Monitor for irregular API activity: Calls like GetSendQuota or CreateEmailIdentity can signal abuse.
- Adopt automated secret scanning: Detect and revoke exposed keys before they’re used.
- Educate developers: Even a single exposed environment variable can compromise entire projects.
How Secure Remote Access Prevents Credential Exposure
While TruffleNet exploited cloud-level credentials, many of those leaks originated at the endpoint, developers or contractors connecting from unsecured networks. In distributed environments, one weak remote connection can expose sensitive credentials.
To close this gap, companies need to control where and how users access their cloud platforms. That’s where secure remote access solutions become essential.
Strengthening Cloud Access with PureWL White Label VPN Solution
PureWL White Label VPN Solution empowers organizations to secure cloud access without added complexity. With encrypted, authenticated VPN tunnels, it ensures that AWS and developer traffic only passes through trusted endpoints, while remote and contract teams connect through verified, protected sessions.
Service providers and MSPs can deploy it under their own brand to deliver strong identity protection and control. By combining network-layer encryption with access governance, PureWL ensures that every credential is used only from secure, authorized environments.
Final Thoughts
The TruffleNet attack didn’t expose a flaw in AWS, it exposed a flaw in how credentials are managed and monitored. In an age where attackers rely on legitimacy instead of intrusion, visibility and control over who connects, and from where, define the new cybersecurity frontier.
As enterprises modernize their cloud infrastructure, pairing identity protection with secure network access will be key.
PureWL enables exactly that, a foundation where trust is verified, connections are protected, and the next TruffleNet-style attack is stopped before it begins.