The 2025 Discord data breach has sparked concern among individuals and businesses that rely on the platform for communication and community building. Unlike past rumors about Discord account takeovers, this event was a confirmed security incident tied to a third-party vendor. Attackers gained access to a support platform used by Discord, exposing information shared by users who contacted customer support.
This case is now widely referred to as the Discord customer support data breach exposes user information incident. While Discord’s core infrastructure, servers, and direct messages remained secure, the breach highlighted how support ecosystems and external vendors can introduce risk.
For organizations managing user data or operating online platforms, this incident offers valuable lessons about supply chain security, data handling policies, and proactive communication with affected users.
- Attackers breached a third-party customer support vendor used by Discord, not Discord’s main servers.
- Exposed data included names, email addresses, support ticket content, partial billing details, and some ID images.
- Passwords, chat history, and complete payment details were not affected.
- Users should watch for phishing attempts and enable multi-factor authentication.
- Businesses should strengthen vendor access controls and use encrypted communication channels such as white-label VPN solutions.
- PureWL enables platforms to add secure, branded VPN protection quickly.
What Happened in the Discord Data Breach?
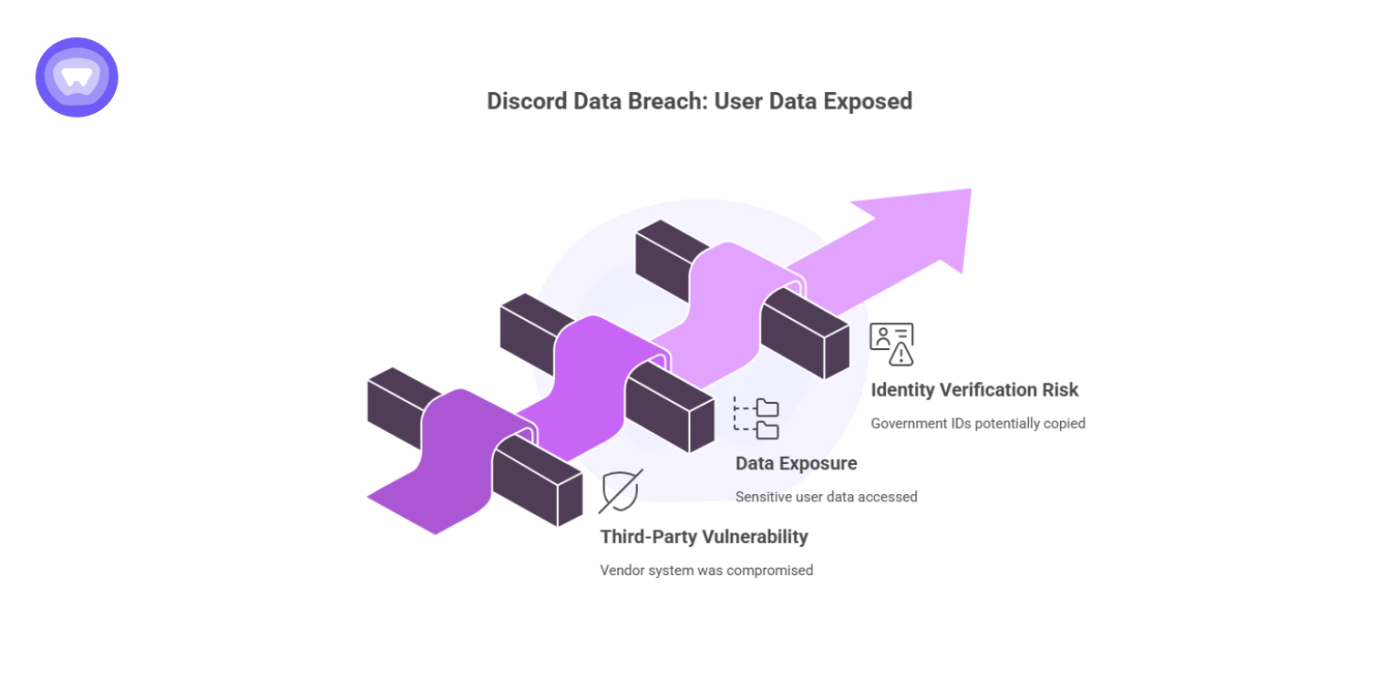
Attackers gained unauthorized access to a support system operated by a third-party vendor. The compromised environment handled user help tickets and identity verification files. While Discord’s infrastructure stayed intact, the attackers viewed and potentially copied:
- Full names and usernames
- Email addresses used in support requests
- Support ticket text and file attachments
- Partial billing details for some customers
- A limited number of government ID scans submitted for account verification
This information is valuable to threat actors who craft phishing campaigns targeting affected users.
Scope of Exposure
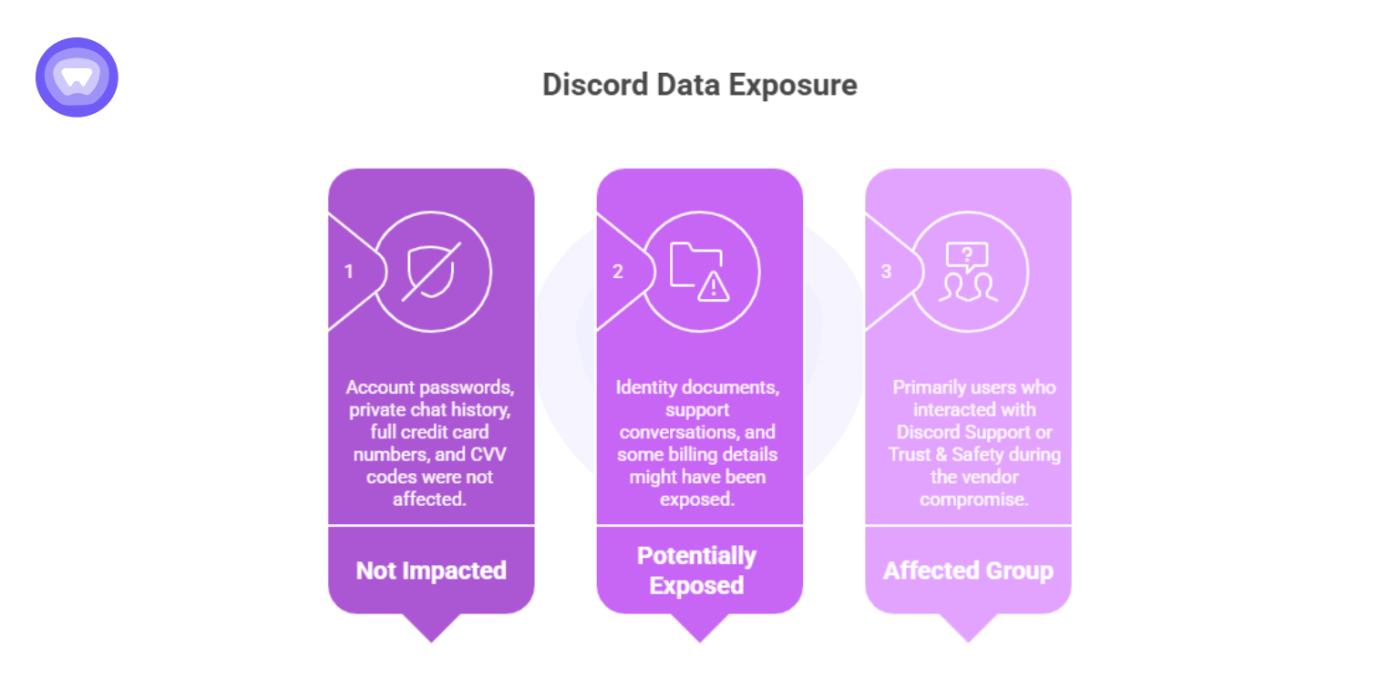
Discord confirmed:
- Not impacted: account passwords, private chat history, full credit card numbers, and CVV codes.
- Potentially exposed: identity documents, support conversations, and some billing details.
- Affected group: primarily users who interacted with Discord Support or Trust & Safety during the time the vendor was compromised.
The breach illustrates the risk of depending on vendors to handle user personally identifiable information (PII).
Lessons for Platform Operators
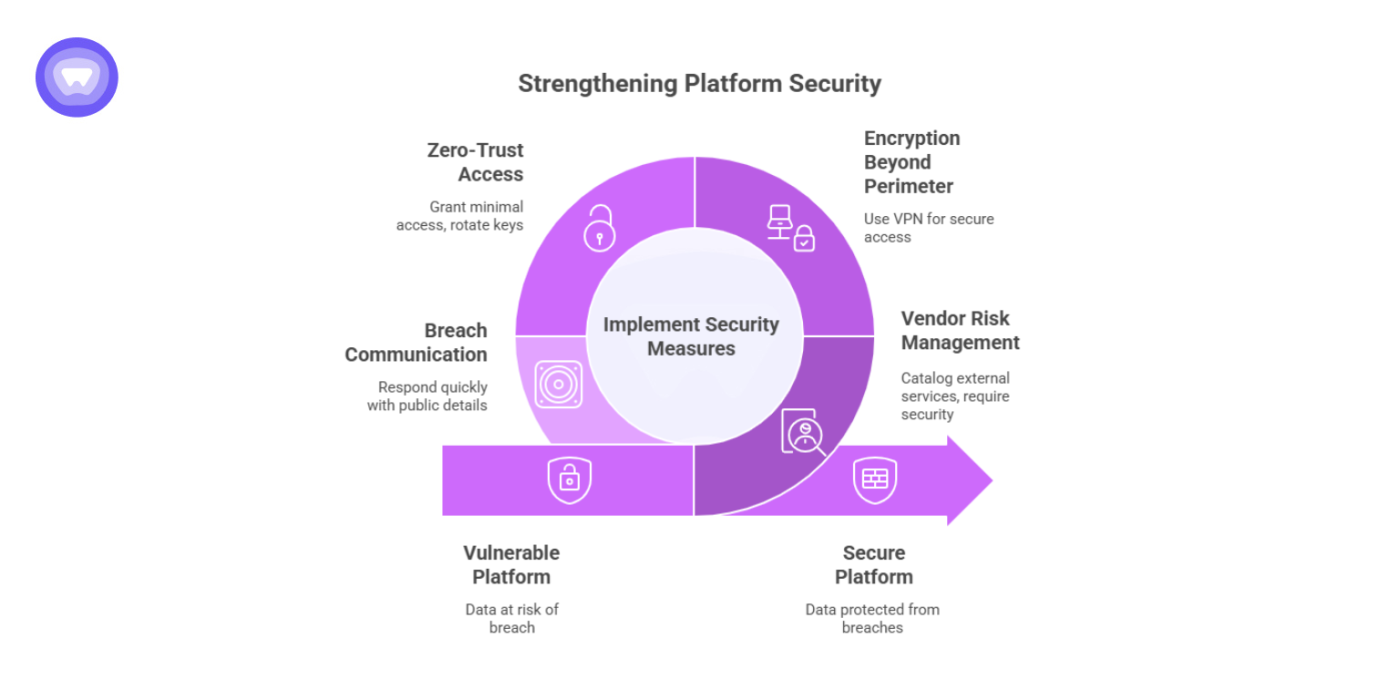
Here is everything that you can learn from this breach:
Vendor Risk Management
Catalog every external service with access to user or operational data. Require documented security controls, timely updates, and penetration testing.
Encryption Beyond the Perimeter
Use encrypted tunnels and secure remote access for all staff and contractors who reach support systems. A white-label VPN can enforce encrypted sessions without requiring an in-house build.
Zero-Trust Access
Grant the smallest possible level of access. Rotate keys and credentials regularly. Monitor logs for unusual support desk activity.
Breach Communication
Discord responded quickly with notifications and public details. Timely disclosure maintains credibility when incidents occur.
Guidance for Individual Users
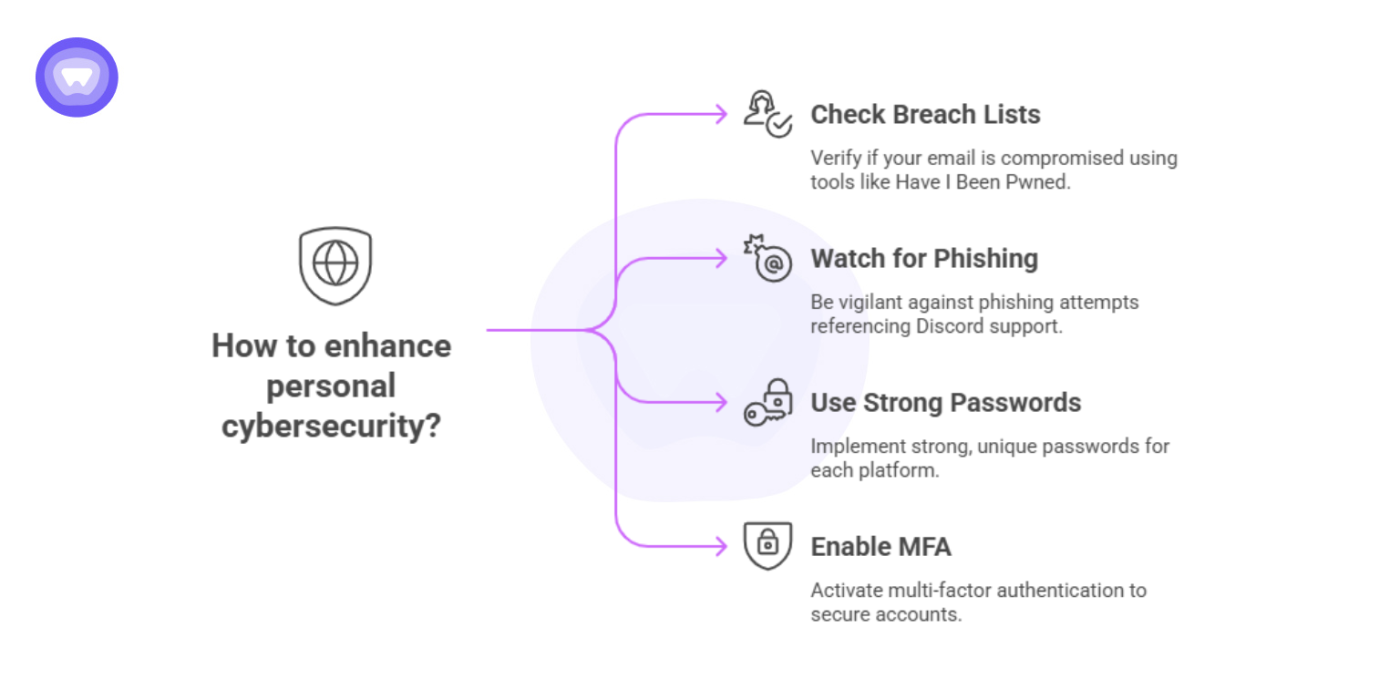
- Check whether your email appears in known breach lists using trusted tools such as HaveIBeenPwned.
- Watch for phishing attempts that reference your Discord support interactions.
- Use strong, unique passwords for every platform.
- Enable multi-factor authentication (MFA) to limit the impact if credentials are ever stolen.
Why VPN Integration Reduces Breach Impact?
Sensitive administrative and support traffic should not move across open networks. VPN integration creates encrypted tunnels between staff, contractors, and internal tools. This prevents attackers from intercepting or manipulating traffic even if an external platform is compromised.
Benefits for SaaS and Digital Platforms
- Secures API calls and admin dashboards
- Protects remote support teams
- Reduces risk of lateral movement after vendor compromise
- Builds user confidence through visible privacy protection
Turning Security into a Feature
Modern SaaS customers evaluate platforms on privacy and security posture. Offering built-in, branded VPN protection increases trust and retention. Building such infrastructure internally requires months and significant capital.
PureWL allows companies to:
- Launch a fully branded VPN service within weeks
- Offer multi-platform apps (Windows, macOS, iOS, Android)
- Secure support and administrative operations
- Provide encrypted access for end users as a premium feature
Adding this layer strengthens compliance, protects vendor integrations, and becomes a marketable differentiator.
Conclusion
The Discord data breach highlights how vendor security weaknesses can compromise user trust even when the core platform remains intact. Businesses should maintain strict oversight of external tools, secure all traffic with encryption, and give staff controlled, audited access to sensitive systems.
PureWLl enables SaaS providers, ISPs, and digital platforms to add enterprise-grade VPN protection under their own brand. It shortens time to market, strengthens privacy promises, and converts security from a cost center into a competitive advantage.


